Crypto ransomware attacks have become the bogeyman of 2024, with cybercriminals exploiting the anonymity and decentralized nature of cryptocurrencies to inflict massive financial damage on businesses and individuals alike. Among the alarming rise in these attacks, one incident has cast a long shadow: the record-breaking $75 million payment to the notorious Dark Angels group. This attack has not only raised eyebrows on the increasing boldness of these cyber criminals but has also featured the urgent need for effective solutions to curb such nefarious schemes and trickery.
The ‘Triumph’ of Crypto-Ransomware In 2024
Ransomware, a type of malicious software designed to block access to a computer system until a sum of money is paid, has grown dramatically with the advent of cryptocurrencies. In 2024, these attacks reached unprecedented levels, fueled by the growing sophistication of cybercriminals and the widespread use cases of digital currencies.
"Our analyses reveal that a few organized ransomware gangs dominate the [#crypto] space and have evolved into sophisticated firm-like operations with physical offices, franchising, and affiliation programs."https://t.co/plQLcCLQCs
— #DisruptionBanking (@DisruptionBank) August 24, 2022
According to recent reports, the number of ransomware attacks surged by over 50% compared to the previous year, with the average ransom payment exceeding $500,000. In fact, according to a report by the leading blockchain analysis company Chainalysis, overall illicit activity dipped by 19.6% — from $20.9 billion to $16.7 billion —and hacking and ransomware attacks bucked the trend. The total value of crypto pilfered by July 2024 exceeded $1.58 billion, marking an alarming 84% jump compared to the same period in 2023.
One of the most concerning aspects of this rise is the increasing success rate of these attacks. The Chainalysis report further revealed that while hacking incidents are up slightly (2.8% from last year), the real concern is that the average amount of money stolen in each hack has nearly doubled. We’re talking $5.9 million per hack in 2023 versus $10.6 million in 2024. That’s a whopping 79.5% increase. As one expert said, “Cybercriminals are no longer just a nuisance—they’re a full-blown crisis.” The anonymity provided by cryptocurrencies like Bitcoin (BTC) and Monero (XMR) has made it nearly impossible for authorities to trace the funds, allowing these criminals to operate with relative impunity.
The FBI has issued warnings these past days in August on even new rising ransomware threats from groups like the BlackCat gang, WannaCryand Scattered Spider, with the possibility of escalation.
🚨🇺🇸 RANSOMWARE ATTACKS PARALYZE MAJOR COMPANIES, FBI WARNS OF EVOLVING CYBER THREAT
— Mario Nawfal (@MarioNawfal) August 12, 2024
Ransomware attacks have severely impacted various sectors, including hospitals, tech companies, and Las Vegas casinos, costing millions in damages.
The FBI warns of a new threat: Scattered… pic.twitter.com/aWowjUhgOL
The Dark Angels Group
Among the various cybercriminal groups, the Dark Angels — purported to be a Russian-based cybercrime syndicate, initially connected to the Babuk ransomware’s source code — have trumped as one of the most feared, with the launch of their victim data leak site, Dunghill Leak, only in April of last year — a show of force and lethality to make good on their threats at any time.
Known for their ruthless tactics and more stringent demands, they made headlines in 2024 with a $75 million ransomware attack.
The details of this incident are chilling as this payment nearly doubled the previous $40 million record for the highest publicly known ransomware payout by insurance giant CNA —a 96% and 335% year-over-year (YOY) huge upside compared to the 2023 and 2022 ransom size. CNA suffered an Evil Corp ransomware attack in late March of 2021, a Bloomberg report shows.
We can confirm that early this year we saw the largest ransomware payment ever at $75M. The "big game hunting" trend we discussed in our 2024 crime report – fewer attacks on larger targets with deeper pockets – is becoming more pronounced. https://t.co/Z0yvg3Zvp2 pic.twitter.com/4FsivojtA5
— Chainalysis (@chainalysis) July 30, 2024
The Dark Angels targeted a major multinational corporation, encrypting critical data and threatening to destroy it unless the ransom was paid in BTC. After days of failed negotiations and mounting pressure, the anonymous company — believed to be pharmaceutical giant AmerisourceBergen Corporation (now Cencora) — was left with no choice but to comply with their demands, transferring the largest ransom payment in history. The incident was a major wake-up call for the industry, as companies worldwide realized they were potential targets. The cloud security firm Zscaler stumbled upon this record-breaking payout early in 2024. This incident now holds the dubious honor of being the largest ransomware payment by a company in history.
Citing the Zscaler report, the top ransomware target, making up almost half of all attacks, remained the USA, with the United Kingdom a distant second place (5.92%), with Germany (4.09%), Canada (3.51%), and France (3.26%) following behind.
Adding to this, chief security officer at Zscaler, Deepen Desai said, “The increasing use of ransomware-as-a-service models, along with numerous zero-day attacks on legacy systems, a rise in vishing attacks, and the emergence of AI-powered attacks, has led to record-breaking ransom payments.”
Avoiding Headlines
The Dark Angels group, which first reared up its ugly head around May 2021-22, is notorious for its highly targeted approach. The group succeeds in its stratagem thanks to a combination of sophisticated hacking techniques and the strategic use of cryptocurrencies. Crypto-ransomware attacks typically involve phishing emails or exploiting software vulnerabilities to gain access to a victim’s system. Once inside, the attackers encrypt sensitive data and demand a ransom in crypto coins, which is difficult to trace.
The Dark Angels, in particular, are known for their meticulous planning and execution. They often spend months studying their targets, identifying weak points, and developing highly personalized attacks. Thus, unlike most ransomware groups that cast a wide net, Dark Angels typically set their sights on a single large company at a time. Once they infiltrate and compromise a target, they decide whether to lock up the victim’s files or servers one at a time, initially using Windows and VMware ESXi encryptors but later moving to a Linux encryptor by Ragnor Locker. They avoid the typical ransomware affiliate model of hiring extra hands and maintaining a low profile, focusing on quiet mass data theft rather than disrupting operations.
“They really don’t want to be in the headlines or cause business disruptions,” senior director of threat intelligence at ThreatLabz, Brett Stone-Gross, said. “They’re about making money and attracting as little attention as possible.”
This, combined with the anonymity of cryptocurrencies, makes it highly challenging for law enforcement to track them down. And the results are devastating. In most cases, the Dark Angels group pilfers a vast amount of data, typically in the range of 1-100TB, depending on the size of the business or organization.
The rise of crypto-ransomware has exposed huge vulnerabilities in both technology and regulation. “It’s a cat-and-mouse game,” says a cybersecurity analyst. “As soon as we develop new defenses, they find ways around them.”
Keeping Constant Tabs
To shield against ransomware attacks and bounce back from them if they occur, the National Institute of Standards and Technology (NIST) has published an infographic offering a series of simple tips and tactics. These include using antivirus software at all times, keeping all computers fully patched with security updates, and using security products or services that block access to known ransomware sites on the internet.
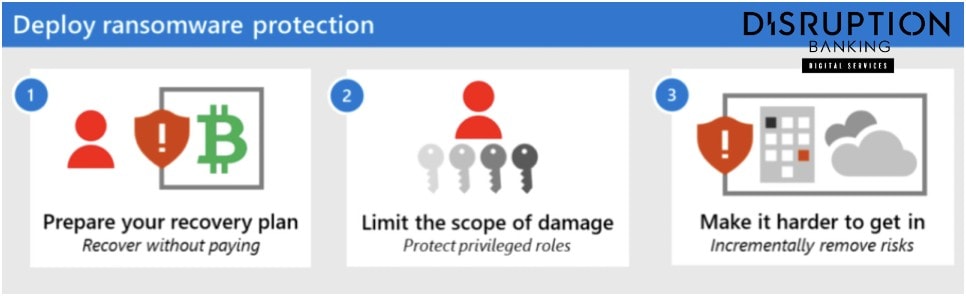
Recommended mitigation prioritization. Image via: Microsoft Security
Besides these, Microsoft experts suggest a multi-layered defense strategy, such as ensuring that antivirus software includes ransomware protection and considering additional software dedicated to ransomware defense. Organizations are also advised to deploy artificial intelligence-enabled email security tools and endpoint security software and to partner with firms offering managed detection and response (MDR) services.
As we progress, ransomware hackers will likely keep looking for easy, deep-pocketed targets and quickly exploit new weaknesses. This means companies need to make it a top priority to fix vulnerabilities quickly and have a fast response plan in place to reduce the risks of these types of attacks.
Want to stay one step ahead and get a handle on the Dark Angels ransomware and the bigger picture of crypto-ransomware attacks? It’s non-negotiable to stay up-to-date on the latest developments and security solutions in the space. By staying vigilant, individuals and organizations can better protect themselves against these constant cyber threats.
Author: Ayanfe Fakunle
The editorial team at #DisruptionBanking has taken all precautions to ensure that no persons or organisations have been adversely affected or offered any sort of financial advice in this article. This article is most definitely not financial advice.