Could it be the largest theft in history? On Friday last week, Bybit, a Dubai-based cryptocurrency exchange, was hacked and approximately $1.5 billion worth of ETH was stolen. It stands as the largest theft in history. Larger by far than Mount Gox collapse of 2014. Could the Lazarus Group be behind the $1.5 billion Bybit crypto heist?
It was supposed to be such a good day. On Friday, Coinbase announced that the SEC had agreed to drop its enforcement case. Brian Armstrong, Coinbase co-founder and CEO, wasn’t quite as derogatory about the SEC as Ripple’s Brad Garlinghouse a few days before, but he did share with CNBC how the case marks a “huge day” for Coinbase and the crypto industry at large. Little did he know that later in the day his words would come back to haunt him.
Bybit Didn’t Need a Crypto Heist
The cryptocurrency exchange affected by last Friday’s hack was Bybit, one of the leading exchanges in the world with almost 5 million followers on X. The company was accused of treading a fine line with Russian users last year. It has also started serving citizens of China who can prove they live outside the country, which may be unpopular with some in Beijing. Finally, Bybit saw substantial growth after targeting former customers of FTX, the failed crypto exchange. It made a lot of money in 2024 and does this by offering very low fees compared to other exchanges.
But, during the evening (local time) on Friday last week, everything changed for Bybit. Ben Zhou, co-founder and CEO, reported on X that a transfer between wallets had been ‘musked’. Not Elon Musked, more ‘masked’ with some fancy UI. The attackers replicated a payment link that the three signatories regularly used for transferring digital assets between cold and hot wallets. Everything looked identical.
Bybit ETH multisig cold wallet just made a transfer to our warm wallet about 1 hr ago. It appears that this specific transaction was musked, all the signers saw the musked UI which showed the correct address and the URL was from @safe . However the signing message was to change…
— Ben Zhou (@benbybit) February 21, 2025
The Victim – Ben Zhou
Zhou was quick to react. He had to be. With cryptocurrency exchanges there are always online users monitoring whale activity as well as smaller transactions. There were in the case of Bybit’s hack. The removal of 401,346 ETH from circulation, almost 0.5% of global supply, is going to get noticed. He had to react.
The attack hit the tech entrepreneur hard. He immediately woke up his entire management team (on a Friday night local time in Singapore). Zhou was worried there might be a bank run and wanted to react as quickly as possible. And, once his management team were engaged, his next job was to ensure that he could find funds to make up any potential shortfall in ETH.
Zhou took to X with a live stream to help calm down the market. Some of Bybit’s customers had already had a bad experience with FTX just a few months ago, and what had happened to Bybit looked like it might play out in the same way. Communication has been excellent from the CEO of Bybit. He did more than you could expect in galvanizing the organization to address the hack.
The Defendant – The Lazarus Group
It’s important to note that there is no actual hard evidence to prove who was responsible for the hack. There are similarities in behaviours. Levels of sophistication that only of a very small group of bad actors on the market can achieve. To know that there were three signatories. How they behave. Who they are. And when the exact moment was to strike.
So far, all the evidence points at one group. A group of ‘cyber warriors’ operating out of North Korea.
The FBI, as well as many other agencies, has been following the Lazarus Group’s cyber-attacks for many years. According to the FBI the group is comprised of North Korean cyber actors and has been responsible for numerous attacks on crypto companies. The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned the Lazarus Group in 2019.
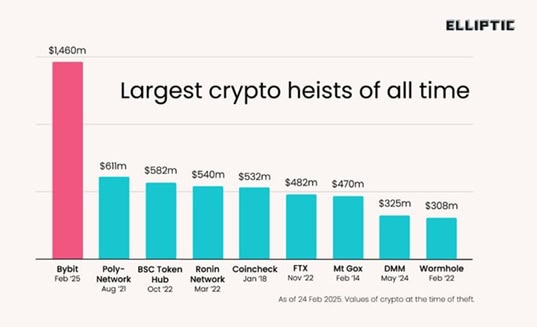
In 2024 the leading bug bounty and security services platform for web3, Immunefi, published a report about the Lazarus Group. In the report the company shared how it had “seen a loss of $1.9 billion across the web3 ecosystem from 2021 to 2023, due to the Lazarus Group. Most of the sum came from the attack on Axie Infinity’s Ronin Network, with a loss of $650 million, and Poly Network, which suffered a $600 million loss.”
The types of techniques used by the Lazarus Group include:
- Phishing
- Social engineering
- Exploration of smart contract vulnerabilities
- Exploration of validator nodes
- Unauthorized access
- Stolen private keys
- API exploitation
The North Korean cyber warriors have even used fake LinkedIn job offers to steal user data.
Elliptic, a leading provider of cryptoasset transaction and wallet screening, has provided specific research which they say points to the Lazarus Group.
The Evidence
Elliptic suggests that the Bybit theft bears similarities to previous Lazarus Group activities. The company has worked around the clock with Bybit, cryptocurrency service providers and fellow investigators like @ZachXBT, to trace and block the stolen funds from being paid out.
Elliptic’s research points to how the laundering of the stolen ETH follows a pattern. Some of the staked ETH which was stolen has been exchanged for ETH through decentralized exchanges. Much of it has then been converted to bitcoin using eXch, another cryptocurrency exchange.
From what can be seen Bybit isn’t popular with all of the digital assets ecosystem. Zhou did post earlier today about how Bybit had received $1.23 billion through loans, whale deposits, and ETH purchases. eXch is less inclined to help due to bad history between the exchanges.
There are, however, some signs that lost funds are being frozen before they can be paid out or moved further by other exchanges. $42.89 million has been recovered in one day due to teamwork in the ecosystem.
A coordinated effort led to the freezing of $42.89M in just one day. Thanks to the following teams for their swift action: @Tether_to: Flagged address and froze 181K USDT @THORChain: Blocked the blacklist @ChangeNOW_io: Froze 34 ETH @FixedFloat: Froze 120K USDC + USDT…
— Bybit (@Bybit_Official) February 23, 2025
All the signs suggest that the North Korean Lazarus Group carried out the $1.5 billion crypto heist. As time goes on the crypto community is getting more familiar with the name of this group of cyber warriors. Nobody likes a bad player. All participants of the web3, DeFi and wider crypto communities need to stay aware and hope that the future won’t hold any other nasty surprises.
Author: Andy Samu
#cyberwarrior #lazarusgroup #bybit #ETH #hackers #cybersecurity #NorthKorea #crypto #community
See Also:
Does the ION Group Ransom Attack mean more Regulation? | Disruption Banking
Why Are Pig Butchering Scams On The Rise? | Disruption Banking
Kraken Turns Its First Hack Into White Hat Firm’s PR Nightmare | Disruption Banking















